Essential Email Knowledge: Protecting, Organizing, and Thriving
What Do I Need to Know About My Email?
Your email is a pivotal component of your digital presence and communication. Here is Net10.net’s list of what you need to know about email management to protect, organize, and communicate effectively with clients and friends online.
Account Security: Protect Your Digital Identity
- Ensuring the security of your email account is paramount. Strong, unique passwords are your first line of defense.
- Steer clear of easily guessable options like “password123.”
- Take it up a notch with two-factor authentication (2FA). It adds an extra layer of security by verifying your identity through a code sent to your mobile when logging in.
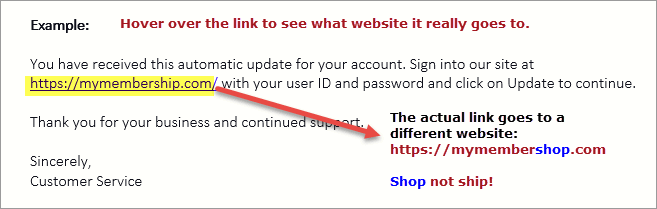
Phishing Awareness: Dodge the Deceptive Hooks
- Watch out for emails from suspicious senders or requests for personal information and financial details.
- Verify the sender’s email address and be cautious about emails with misspelled domains or suspicious URLs.
- Don’t click on links or download attachments from unknown sources when in doubt.
- To learn more, see our Email Phishing Attacks — And Preventative Methods blog.
Email Classification: Managing Your Inbox Effectively
- Understanding how your email service classifies messages is vital.
- Regularly check your spam folder for legitimate emails that may have been incorrectly categorized.
Backup Your Emails: Safeguard Your Valuable Data
- Regularly back up crucial emails to prevent data loss.
- Most email services offer email backup and archiving options.
Privacy and Encryption: Secure Your Confidential Messages
- Consider encrypted email services for enhanced privacy.
- Some providers offer end-to-end encryption.
- When sharing sensitive information, opt for secure methods like password-protected files or encrypted messaging apps.
Email Clients: Choose What Works for You
- Select an email client that aligns with your needs, whether a web-based service like Gmail or Outlook or a desktop client like Mozilla Thunderbird.
Email Organization: Keep It Tidy
- Organize your emails with folders and labels to quickly find important messages.
- Utilize filters and rules to sort and categorize incoming emails automatically.
Email Etiquette: Be a Polite Communicator
- Follow proper email etiquette with clear subject lines, concise and polite language, and appropriate formatting.
- Avoid excessive use of capital letters, as it can come across as shouting.
Attachments: Be Mindful of Sizes
- Pay attention to the size of email attachments, as large files can pose problems.
- Consider using file-sharing services like Dropbox or Google Drive for larger attachments.
Regular Maintenance: Keep It Clean
- Periodically clean up your inbox by deleting or archiving old and unnecessary emails.
- Monitor your email storage limits, especially with free email services.
Mobile Access: Stay Connected Securely
- Ensure your email is accessible and secure on mobile devices.
- Install the official email app or configure your email client for mobile use.
Spam and Unsubscribe: Tame Your Inbox
- Mark spam emails as spam to help train your email provider’s filter.
- Use the unsubscribe option in legitimate marketing emails to reduce unwanted messages.
Recovery Options: Plan for the Unexpected
- Familiarize yourself with the account recovery process if you forget or lose your email account password.
Regular Updates: Stay Secure
- Keep your email client and device software up-to-date to protect against security vulnerabilities.
Legal Considerations: Know the Rules
- Understand email’s legal and regulatory aspects, especially if you use it for business purposes, to ensure compliance with data protection laws like the General Data Protection Regulation (GDPR), which protects individuals’ fundamental rights and freedoms, particularly their right to protection of their personal data.
Ready To Safeguard Your Email And Data With Net10.net?
- Discover NET10’s Premium Email offering — a cost-effective alternative to Office 365 or G Suite, featuring accurate data backups and top-notch data recovery assistance.
- While major cloud providers may not guarantee data recovery in all cases, NET10 stands by its customers and will assist in recovering any data hosted by us.
Contact Us to learn more about Net10’s Email Hosting Services and take control of your email security today!