The Crucial Role of Cyber Security In Protecting Your Data
What Exactly is Cyber Security?
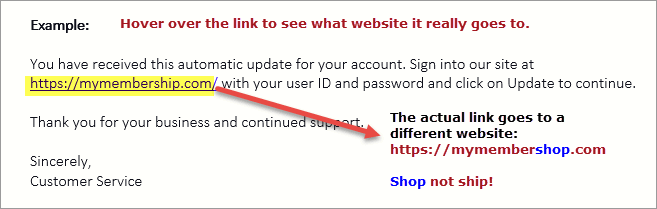
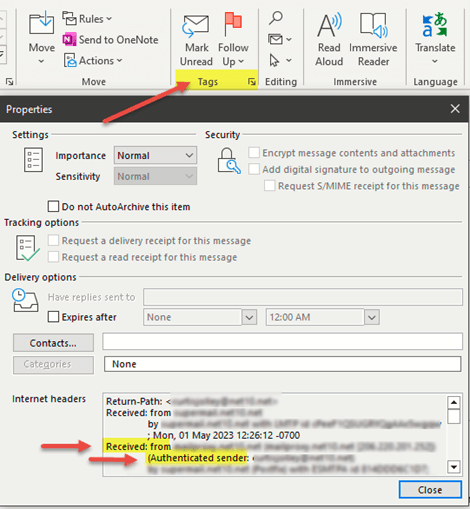
In the age of digital dominance, where information is the new currency, the importance of cyber security cannot be overstated. As we become increasingly dependent on technology, our reliance on computer systems, networks, programs, and data has skyrocketed. With this dependency comes the pressing need to fortify our digital assets against potential threats and cyber-attacks. Let’s take a look into the world of cybersecurity and information security, exploring how they act as the guardians of our virtual domains. We’ll shed light on Net10.net Internet Services, a leading ally in the battle for online security.
Understanding Cyber Security
Cybersecurity is a comprehensive approach to protecting computer systems, networks, programs, and data from digital attacks. These attacks come in various forms, such as viruses, malware, ransomware, and phishing attempts. The goal of cybersecurity is to prevent unauthorized access, minimize damage, and thwart theft of sensitive information.
Key Components of Cyber Security
- Network Security: This involves implementing measures to protect the integrity and confidentiality of data as it travels across networks.
- Endpoint Security: Focused on safeguarding individual devices like computers, laptops, and mobile devices from malicious activities.
- Application Security: Ensuring that software and applications are secure and free from vulnerabilities that cybercriminals could exploit.
- Data Security: Protecting the confidentiality and integrity of data, whether it’s stored or in transit.
- Identity and Access Management (IAM): Controlling and managing user access ensures that only authorized individuals can access sensitive information.
The Role of Cyber Security In Today’s Online World
As we conduct more aspects of our lives online, from banking to healthcare to business applications and communication, the need for robust cybersecurity has never been greater. Without effective protection, our personal and professional information is at risk of being compromised, leading to financial loss, identity theft, and reputational damage.
Net10.net Internet Services: Your Trusted Partner in Cyber Security
When it comes to hosting your website projects, choosing a secure and reliable service cannot be overstated. Net10.net Internet Services is a beacon of trust and security in the vast digital landscape.
Net10.net Security Features
- SSL Certificates: All Net10.net hosting plans come with SSL certificates, ensuring that data exchanged between the user and the website remains encrypted and secure.
- Firewall Protection: Advanced firewall measures are in place to detect and block malicious traffic, keeping your website safe from unauthorized access.
- Regular Backups: Net10.net takes proactive measures to regularly back up your data, providing a safety net in case of unforeseen events.
- 24/7 Monitoring: Constant surveillance ensures that any suspicious activity is identified and dealt with promptly.
Fortify Your Digital Presence with Net10.net
In a world where cyber threats are evolving at an alarming pace, the importance of a secure online presence cannot be overstated. By choosing Net10.net Internet Services, you’re not just hosting your website; you’re fortifying it against potential cyber threats. Make the smart choice today and entrust your digital assets to a service that prioritizes your security.
In the ever-evolving digital landscape, cybersecurity remains our first line of defense. Let’s join forces to protect your online business and make it a safer place for everyone. Contact Net10.net now and take the first step towards a safer online journey. Your digital fortress awaits!