
Email Phishing Attacks — And Preventative Methods
Email phishing attacks are Internet attacks where the attackers send emails that appear to be legitimate. However, their goal is to trick you into revealing sensitive information, such as passwords or financial details. Some can install harmful software on your computer or mobile devices. Here are some steps you can take to avoid falling victim to email phishing:
Be vigilant about emails from unknown senders: If you receive an email from an unknown sender or an email that looks suspicious, do not click on links or download any attachments.
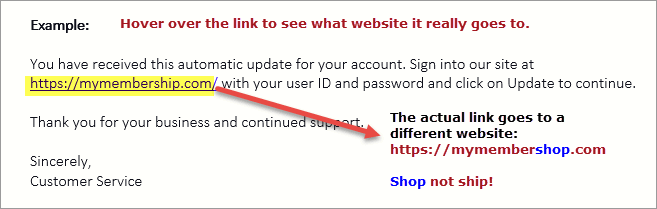
Check links and attachments before clicking on them: Put your cursor over a link and look to see if the URL is secure. It should start with https://. Also, look carefully at the URL, as It may not be the website you visit after clicking the link. Tricks include misspelling words you may not catch and using a combination of letters such as an r and an n to look like an m, like this: rn. Clicking fake links means downloading a virus or allowing someone to install ransomware and take control of your device. If there is an attachment and you are unsure what it is about, don’t open it. That is another way someone can install a virus or ransomware on your computer or mobile devices.
Verifications: It is always a good idea to verify a request via phone or other communication channels (NOT one referenced in the suspicious email, but one that is known to you from your personal or business relationship with the sender). For example, title and escrow companies always do this by requiring a phone call to their office to verify wire instructions.
Use anti-phishing tools: Use anti-phishing tools provided by your email service provider or install anti-phishing software to help detect and block phishing attempts. See Tip #1 below.
Check the sender’s email address: Check the sender’s email address carefully to ensure that it matches the legitimate email address of the company or organization they claim to represent. See tip #2 below.
Don’t provide personal information: Never provide personal information, such as passwords or financial details, in response to an email request.
Keep software up to date: Keep your operating system and antivirus software up to date to protect against known vulnerabilities.
Be wary of urgent requests: Emails that demand an immediate response or threaten dire consequences if you don’t comply are a red flag. Do not respond and simply delete them. Mark as spam and block them.
Net10.net Quick Tips:
Consider upgrading your security to include a Virtual Private Network (VPN). You can still use your email accounts safely without one. However, the risk of getting phishing or malicious emails is significant. With a VPN, you can eliminate many dangers, and you will be able to make your email communication safe, secure, and private for you. We highly recommend ExpressVPN. Let us know if you have VPN questions. We are always glad to help!
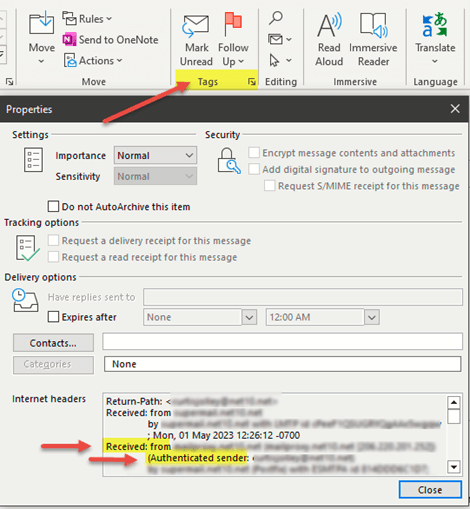
Email headers contain lots of information, including sender/recipient details. Do a quick review to see if the sender’s information matches what you see in the from section of the message. If not, it may be a phishing attack. Here is an example from Outlook 365:
Click on the Message tab and select Tags to view Properties.
Next, find the Internet Headers section.
Look at the Received From details to determine who sent the email.
If something doesn’t look right, you may not want to respond!
If you don’t use Outlook, do a quick Google search for View Email headers and type the name of the app you use for step-by-step instructions, such as Gmail. Like this: How to view email headers for Gmail.
We hope this information about email phishing is helpful. If you have questions or other topics you want Net10.net to write about in our blog, just let us know at support@net10.net.
