Ransomware And How To Protect Your Data
Protecting your data from a ransomware attack requires a combination of preventive measures and proactive practices. Here are essential steps Net10.net recommends you take to help safeguard your data.
Backup Your Data
Regularly back up any files and data, you want to protect to an external hard drive, offline storage, or secure cloud-based service. Ensure that your backups are not directly accessible from your computer or network to prevent them from being compromised in an attack. You can restore files affected by a virus or hackers using a previous backup. Net10 backs up files daily, weekly, and monthly.
Keep Your Software Updated To Prevent Ransomware/Malware Attacks
Regularly update your operating system, software, and applications with the latest security patches and updates. Many attacks exploit vulnerabilities in outdated software, so staying up to date can help protect you from known vulnerabilities.
Keep Hackers Out By Using Solid And Unique Passwords
Create substantial and complex passwords for all your online accounts, including email, social media, and file-sharing services. Consider using a good password manager to generate and securely store your passwords.
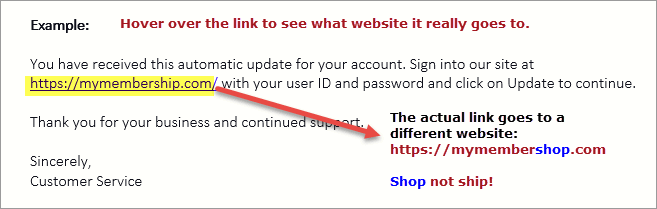
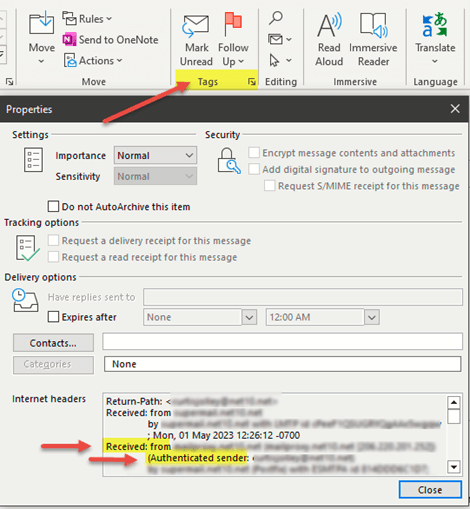
Be Cautious With Emails With Attachments And Links
Avoid opening email attachments or clicking on suspicious links from unknown senders. Be especially vigilant with email attachments that end in file extensions like “.exe” or “.vbs,” as these can execute malicious code.
Use Reputable Security Software
Install and regularly update reputable antivirus and antimalware software on your devices. These programs can help detect and prevent malware infections, including ransomware.
Enable Automatic Software Updates
Enable automatic updates for your operating system and software whenever possible. That ensures that you receive critical security patches on time.
Educate Yourself And Your Team
Stay current about the latest threats, and teach yourself and your team about best practices for cybersecurity. Be cautious about sharing sensitive information online and teach others to recognize and avoid potential risks.
Use A Firewall To Protect From Ransomware Attacks
Enable and regularly update a firewall on your computer or network. Firewalls act as a barrier between your devices and the internet, helping to prevent unauthorized access and filtering out malicious traffic.
Limit User Privileges
Restrict user privileges to the minimum necessary for each individual. That reduces the potential impact of a ransomware, virus, or malware attack by limiting the access attackers have to critical files and systems.
Implement Network Segmentation
Net10 Internet Services can segment your network into different zones with varying access levels and security controls. That can help contain the spread and limit the damage if one part of the network is compromised.
Additional Information
Remember, while these measures can significantly reduce the risk of a ransomware attack, maintaining a proactive and vigilant approach to cybersecurity is crucial. Review and update your security practices to stay ahead of evolving threats. At Net10, we encourage our clients to read our related blogs, such as “What Is Ransomware” and “Email Phishing Attacks — And Preventative Methods.” Contact us if you have any questions. We are always glad to help!